- Telefon: +60 12 809 1368
- E-mel:
Be updated, subscribe to the OpenKM news
Document Security in Companies

Written by Paco Ávila on 05 August 2014
One of the most important reasons why you should implement a document management system in the company is safety.
Factors such as the lack of the amount of files you have, the number of users who can access them without permission or ignore where they are located today, symptoms of poor document management.
We will describe in three steps how, in an agile and fast, the document management software can help solve the various security tasks to facing us.
Selection of confidential files
In this section we will determine which documents are referred to as the most “sensitive” about safety. This process is made during cataloging them and requires meticulous work by staff. Completed this step, selecting files by content, documents “restricted access” would call is made.
With the help of our document management system, we will determine what documents require greater protection either by electronic signature or by restricting access to certain users for download.
Location
It is essential that the selected files in the previous step are located in folders and subfolders within our document management system, with restricted access.
To do this, we create a box document classification where the degree of security of our documents and indicate which users can access them.
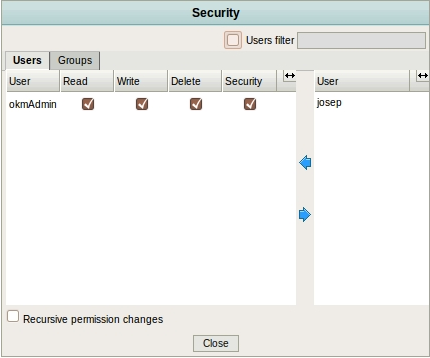
Access Permissions
In this passage indicate, by document manager, which users have restricted access to certain sensitive documents and what not.
This process is easier if we have a good file management software as a OpenKM.
OpenKM and security
OpenKM is a Java EE application using Spring Framework. The module is the most important layer of security – Spring Security – that centralizes management of access allowed to users based on their credentials. The security control is vested in a AccessManager module that implements the logic of safety assessment in the application. The Java EE architecture implemented in OpenKM allows to implement custom security logic.
The authentication process in OpenKM can be carried out by CAS (Centralized Autentication Service), LDAP, or through a database where users are registered service.

